In today’s increasingly complex and interconnected digital landscape, understanding and mitigating cybersecurity risks is a critical priority for organizations. One of the most effective ways to manage these risks is through threat modeling and intrusion analysis assessments. These processes not only help identify vulnerabilities but also guide organizations on how to proactively defend against potential attacks. In this blog, we’ll explore the importance of threat modeling, its components, best practices for implementing it, and how it can be used to strengthen your organization’s security posture.
What is Threat Modeling?
Threat modeling is a proactive approach to identifying, understanding, and mitigating potential security threats in an organization’s system or application. At its core, it aims to protect your organization’s assets, anticipate threat agents (TAs), and determine the controls necessary to mitigate those threats. Let’s explain them!
- Assets: These are the valuable resources within your network or application that you aim to protect. Assets can include sensitive data (e.g., Personally Identifiable Information or financial records), software, hardware, network infrastructure, and intellectual property.
- Threat Agents (TA): These are the entities human or non-human that pose a potential risk to your assets. Threat agents can include external attackers (hackers, cyber criminals), internal actors (employees or contractors), or automated malicious software (e.g., malware, bots). The methods and motivations of these threat agents can vary widely, so understanding who might target your assets is essential.
- Controls: These are the security measures put in place to protect assets from threat agents. Controls include technical measures such as firewalls, encryption, and intrusion detection systems (IDS), as well as procedural measures like access controls, user training, and incident response plans.Effective threat modeling requires a clear structured approach.
Some of the best practices that will help you create an actionable threat model that can inform your security strategies:
1. Define the Scope and Depth of Analysis
The first step in any threat modeling effort is to define the scope of your analysis. This means understanding what assets need to be protected and which parts of your system are most vulnerable. Work closely with stakeholders from across the organization to define this scope. Once the scope is clear, break down the depth of analysis for individual teams, such as development teams, to ensure that they are modeling the threats specific to the software they are building or maintaining. By segmenting the work based on roles and responsibilities, you can focus on the most relevant threats for each part of the system.
2. Gain a Visual Understanding
A key part of the threat modeling process is creating a visual representation of the system architecture. This could include diagrams that illustrate the relationships between major system components, such as: Application servers, Data warehouses, Databases, Network services, Client devices and so on.
Mapping out these components allows you to better understand the flow of data and the interactions between different system elements. Visualizing the system helps you spot potential weak points, such as an unsecured database, weak authentication mechanisms, unpatched software, improper firewall rules, Insufficient security awareness training for users or administrators might lead to social engineering attacks …etc.
3. Model the Attack Possibilities
Once you’ve established a visual representation of your system, it’s time to model the possible attacks. Start by identifying key software assets, security controls, and potential threat agents, and then diagram their locations to create a comprehensive security model of the system. To guide your analysis, consider using a well-known methodology like STRIDE, PASTA, LINDDUN, or choose any methodology that best aligns with your organization’s needs. The right choice will depend on factors like your system’s complexity, your business goals, and the nature of the threats you’re addressing.
Once you have modeled the system, you will have a better idea of what could potentially go wrong (i.e., what the threats are and which assets could be affected by these attacks.)
4. Identify ThreatsTo effectively identify threats, ask critical questions such as:
-> Are there paths where a threat agent can reach an asset without going through a control?
-> Could a threat agent bypass this security control?
-> What must a threat agent do to bypass this control?
These questions will help you build a comprehensive list of potential attacks that could target your assets.
5. Create a Traceability Matrix of Missing or Weak Security Controls
Once you have identified the potential threats, create a traceability matrix that links each asset to its corresponding threat agent and controls. This matrix will help you track the security gaps and highlight areas where controls are either missing or weak. For example, you might find that an Active Directory environment is vulnerable because it allows users to maintain weak or default passwords, and there’s no enforced policy for password complexity or regular resets.
Your traceability matrix will look something like this: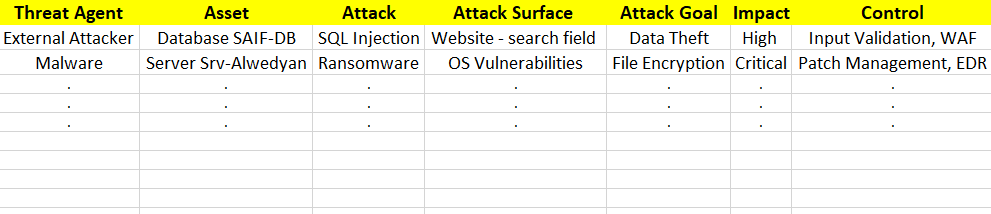
This matrix will help prioritize the implementation of security controls and ensure that each asset is protected against its most likely threats.
Integrating Intrusion Analysis Assessments
While threat modeling focuses on pinpointing potential risks, intrusion analysis assessments dive deeper into how attackers might exploit vulnerabilities using their Tactics, Techniques, and Procedures (TTPs).
By combining threat modeling with intrusion analysis assessments, you gain a more holistic view of your security landscape.This integrated approach enables you to:
-> Identify vulnerabilities that may not have been obvious during the threat modeling process.
-> Test the effectiveness of your current security measures.
-> Refine your controls based on the outcomes of intrusion assessments, ensuring that they are both effective and efficient.
-> Improve incident response capabilities by practicing with real-world attack scenarios.
Conclusion
Cyber threats are continuously evolving, and the impact of a successful attack can be devastating leading to data breaches, financial loss, reputational damage, and operational disruption. Threat modeling is an essential tool in safeguarding your organization’s systems by proactively identifying and understanding potential threats.Did you find this blog useful and want to start enhancing your organization’s security with threat modeling? Let’s connect today and take the first step towards fortifying your defenses!