Over the past years, I have been engaged with different SOC environments, working with diverse technologies, teams, and processes; each leading to a different level of SOC maturity.
Many SOCs have a large number of detection rules and alerts, but struggle to link them back to business risks or compliance drivers. They often face excessive noise, weak detections, and missed threats.
Over time, they accumulate many use cases, rules, and log sources, but frequently lack lifecycle management! what’s still relevant, and what’s stale? Threat actors and attack techniques evolve, but when use cases are not updated accordingly gaps quickly appear. These challenges highlight the need for a structured approach and that’s where the MaGMa UCF (Use Case Framework) comes in.
➊ MaGMa stands for Management, Growth, Metrics & Assessment. These three pillars describe what the framework is built to achieve:
– Manage use cases throughout their lifecycle.
– Grow SOC detection capability over time.
– Measure and assess maturity and effectiveness.
➋ Each use case in MaGMa UCF is described using three layers: Business, Threat, and Implementation to ensure clear traceability from business risk to detection rules:
– Business Layer: Describes why the use case exists; the business driver, risk, compliance, or regulation it supports.
– Threat Layer: Describes what you’re defending against; the adversary, attack scenario, or threat type.
– Implementation Layer: Describes how it’s detected; data sources, correlation rules, SIEM logic, playbooks, etc.
✍️ This structure ensures traceability from business → threat → detection.
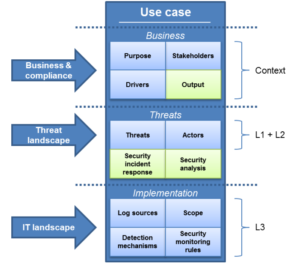
➌ Use cases are also grouped by level of detail (scope):
– L1: High-level business or risk domain.
– L2: Specific threat scenarios within that domain.
– L3: Detailed detection logic or correlation rule.
✍️ This hierarchy helps the SOC organize and manage complexity from strategic to operational levels.
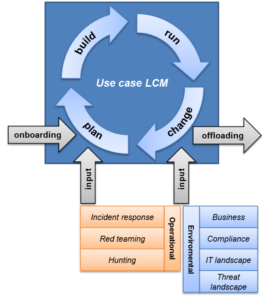
➍ Each use case also follows a defined lifecycle to ensure it remains relevant and effective:
– Onboarding: Define purpose, drivers, and requirements.
– Operational: Active monitoring and detection.
– Maintenance: Periodic review, tuning, and performance checks.
– Offloading: Retire outdated or redundant use cases.
✍️ This prevents rule sprawl and keeps the SOC focused.
➎ MaGMa also includes a metrics and assessment component to measure progress:
– Embedded metrics: Built into the use case (e.g., number of alerts, false positives).
– Control metrics: Show SOC control maturity (e.g., percentage of use cases reviewed quarterly).
– Output metrics: Show outcomes (e.g., reduced response time, improved detection coverage).
✍️ This supports continuous improvement and reporting to management.
In summary, MaGMa UCF provides structured management of SOC use cases through:
📌 3 pillars: Management, Growth, Metrics.
📌 3 layers: Business, Threat, Implementation.
📌 3 levels: L1–L3 hierarchy.
📌 Lifecycle stages and metrics for continuous maturity.
Implementing MaGMa UCF isn’t just an optimization, it’s a strategic upgrade for any SOC that wants to move from reactive alert handling to data-driven, business-aligned cyber defense! Start your MaGMa journey today to structure your detections, measure your maturity, and showcase your SOC’s real value.