In this article, I will demonstrate one of the common techniques used by attackers to escalate their privileges or bypass the detection by injecting a malicious DLL file into a legitimate process.
What is a DLL file?
A DLL is an abbreviation for Dynamic Link Library, which is a type of file that contains objects and functions that other programs can load and use when needed to complete specific tasks. Unlike executable applications like those with the .exe extension, DLL files can’t be run directly but must be called upon by other processes that are already running.
Perhaps one day while you wanted to run a specific application you have seen this error:
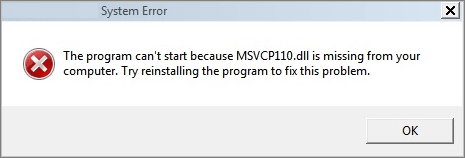
This is because the application you wanted to run needed some objects or functions from the MSVCP110.dll file but couldn’t find it so you needed to download it. I think you have understood the importance of DLL files. But what about their danger?
DLL Injection:
Based on the ATT&CK framework, DLL Injection is a sub-technique of Process Injection that leads to achieving the following tactics: Defense Evasion and Privilege Escalation on Windows environments. (Unix doesn’t use DLLs. Instead, it uses shared object files, “so”).
As the name suggests “DLL injection” primarily tricks an application into calling a malicious DLL file, which then gets executed as part of the target process. You can perform the attack manually either by editing the process address and then injecting the path of the malicious DLL file into the allocated address space or by using tools such as mavinject for example. Once the legitimate process has been executed it will call the malicious DLL that carries the malicious payload to be executed.
Let’s see how we can inject a DLL file called Israel.dll, which has a malicious payload (BTW the name is malicious as well) into a legitimate process called Palestine.exe using mavinject.
What is mavinject?
mavinject is the “Microsoft Application Virtualization Injector,” which is part of App-V (Microsoft Application Virtualization) that allows the delivering of applications to users as virtual applications. It is a PE binary and located at “%windir%System32mavinject.exe” which is digitally signed by Microsoft.
We will use it to perform DLL injection, then we will see how we can create a rule in QRadar Community Edition to catch this suspicious activity.
Injecting the malicious DLL file:
As you see, we have an executable file in C: called Palestine.exe, and it’s currently running as a process with the process ID 4504
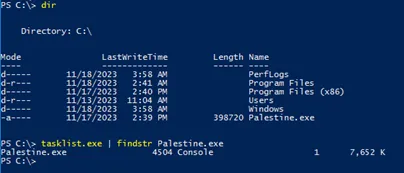
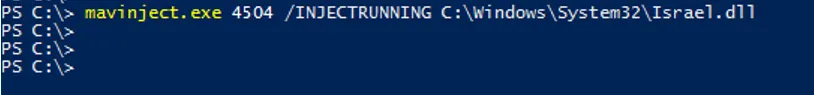
Now let’s use mavinject and specify the target process (Palestine.exe) and the malicious DLL file Israel.dll that is located in C:WindowsSystem32Israel.dll
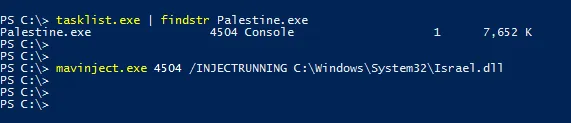
>> mavinject.exe 4504 /INJECTRUNNING C:WindowsSystem32Israel.dll
After executing the tool, we will see some logs have been generated from the victim machine and have been sent to the SIEM, as shown below:
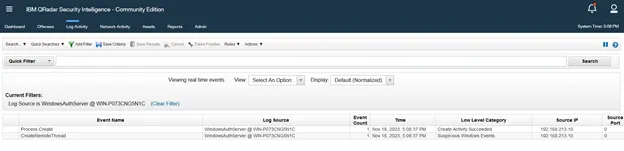
The first one indicates that there is a process that has been created on the compromised server. The second one indicates that there is also a Remote Thread that has been created, which is also related to our activity.
Now we will create a rule based on the above events and perform the malicious activity again to see if there is an offense (alert) that appears in front of the Security Analyst or not.
Creating a rule with the name (Possible DLLs injection via mavinject.exe):
You can give it a name as you like it’s not a matter, but it must be clear and understandable for the analyst.
By going to Rules, then New Event Rule, you will see the Rule Wizard. let’s configure our rule based on events that we have received. I will configure a basic one depending on the process creation QID which is 5001828, and based on “mavinject” and ”INJECTRUNNING” which are valuable strings in our case. As you see in the summary, the rule has been configured:
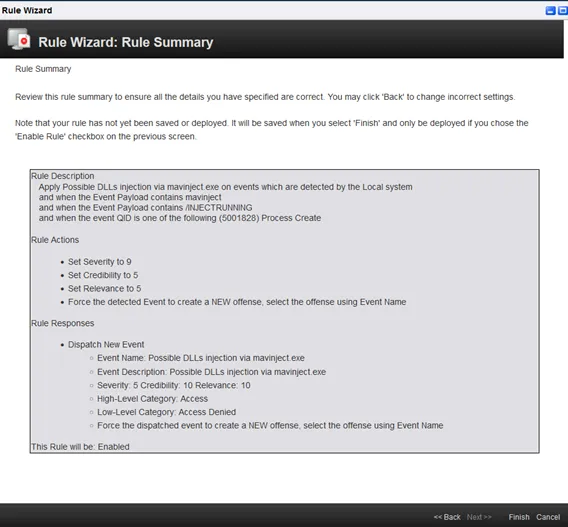
After performing the malicious activity again:
Finally, we can see the generated offense (alert) that is generated by the rule due to it matches with the events, as shown below:
Here comes the job of the SOC Analyst to check this offense and investigate it deeply, then determine if the server is compromised or not.
While There are other tools and methods to execute this technique, but today I have chosen to perform it via mavinject. While exploring DLL injection as a common technique for privilege escalation and defense evasion, our focus centered on mavinject to demonstrate the injection of a malicious DLL into a legitimate process, also the article underscores the importance of the defense measures. In addition to QRadar SIEM rules were showcased as a tool for security analysts to detect and respond to potential DLL injection and other threats in the dynamic landscape of cybersecurity.